We really want to make sure that code running in a DNN website cannot access anything in C:\ no matter what. By default all Application Pool Accounts have some limited permissions which are not needed, so we want to ensure that these cannot be used either.
- On the web server, open the permissions for the drive C:\
- Add Deny permissions for the
IIS_Users group (which contains all automatically generated Application Pool Identities) like this: 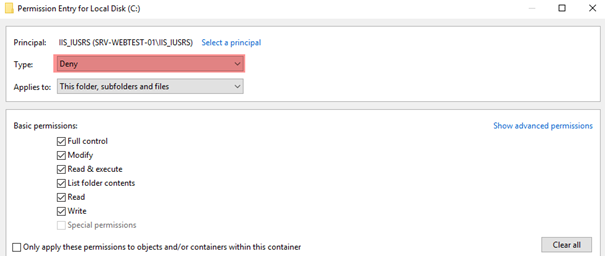
- You'll receive warnings about the following objects, where the Deny cannot be applied. This is ok.
- c:\pagefile.sys
- c:\Program Files
- c:\Program Files (x86)
- c:\Windows
Note that Windows will automatically manage the permissions in C:\Windows etc. as needed, so you don't need to make changes there, unless you are using a setup where the web site files are stored on a remote file store (NAS).
Special Cases
In case you're also hosting your website files on drive C (which you really shouldn't, they should be on another drive), remember to remove this newly added Deny-permission on those folders and harden that folder according to best practices.